Zero Trust#
Later we're going to talk about firewalls, which is a security concept known as "perimeter security" because a firewall creates a virtual "perimeter" around a network. The idea is simple: if you're inside the perimeter, then you must be trustworthy, right? Unfortunately This is being shown to wrong time and time again.
Zero Trust is a security model that states networks should be "perimeterless", although from a technical perspective it doesn't directly do away with firewalls and the concept of perimeter security - you can have both - but it removes the idea that anything on the inside of your network is automatically trusted. Instead, the theory is you trust no one, ever, until they can verify who they are.
Note
Personally, I believe you should have both. Firewalls, VPNs, and more, combined with a zero trust model, allow you to implement serious levels of security and keep networks private. In it purest form, Zero Trust would do away with network boundaries and everything would technically be on the public Internet, which is just silly. If you can keep it unrouteable and private, do so.
What this boils down to is confirming the identity of everyone on the inside of a network. Let's visualise these two concepts.
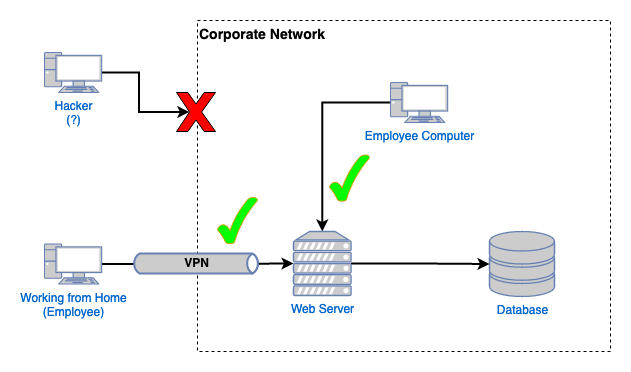
Here we can see two employees are able to access the internal web application because they're "trusted" as they're on the inside of the network (the remote employee is using a VPN to gain a presence on the internal network.) The hacker is denied access as they're not on the inside of the network.
But this model assumes that no devices can ever be compromised or networks cannot be breached. Let's update the diagram to reflect the attacker getting a RAT - Remote Access Trojan - onto one of the employee's computers:
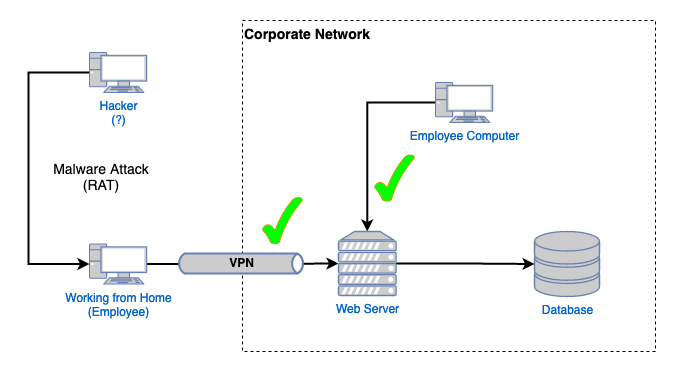
If you've ever done any corporate level security training, as an employee, then you'll have heard of malware and viruses. Above we can see that an attacker has attacked an employee and trick them into installing some software on their system that has given the attacker remote access to it. This isn't some far fetched example, it happens all the time. Using that remote access the attacker is given access to the internal network because they're coming from a "trusted" device.
That's game over for the perimeter security model.
What Zero Trust does here is simple: you must verify yourself all the time. That means providing authentication details on a regular basis using two-factor authentication, Mutual TLS certificates, and more. Although Zero Trust would give an attacker access to the network, they would need to provide authentication details at some point and their attack would falldown completely. Put another way:
"Zero trust is a cybersecurity paradigm focused on resource protection and the premise that trust is never granted implicitly but must be continually evaluated." - Zero Trust Architecture
Note
The above links to an extremely lengthy paper on the concept of a ZTA. It's worth glancing over for sure, but come back to the book and continue your studies here for now.
If an attacker gains access to the network via a compromised system, they must still continuously prove their identity to the internal systems otherwise it's game over for them.
Zero Trust is an old concept, coined in 1994, but it's becoming more of a thing in new environments and even the US government is being pushed hard to implement it.