Transport Layer Security (TLS)#
This protocol is used by HTTP to secure communications over the (public) network. It is, of course, used elsewhere too, but HTTP(S) is a great way of demonstrating how TLS is used.
Note
You'll see SSL - Secure Sockets Layer - but that's been deprecated and replaced by TLS.
Originally (in even today, sadly) HTTP connections operated over TCP/80. Any HTTP connection today is (very likely) going to be a plain text connection. That's not a good idea, and not just because of privacy, but also integrity.
If you transmit something in plain text over a public network (any network, not just the Internet), then other people can (potentially) do two things: see the information and manipulate it.
If someone can see the information then that's dangerous enough. Passwords, credit card details, private conversations, may all be visible.
But what's potentially worse is if someone can change the information. It might not seem like much, but being able to change some information, like political or medical facts, on the fly, to millions of people, could swing an election or kill people.
That's why we encrypt information over the wire. That's why we have HTTPS - HTTPS + TLS.
But how does TLS work? Let's visualise that:
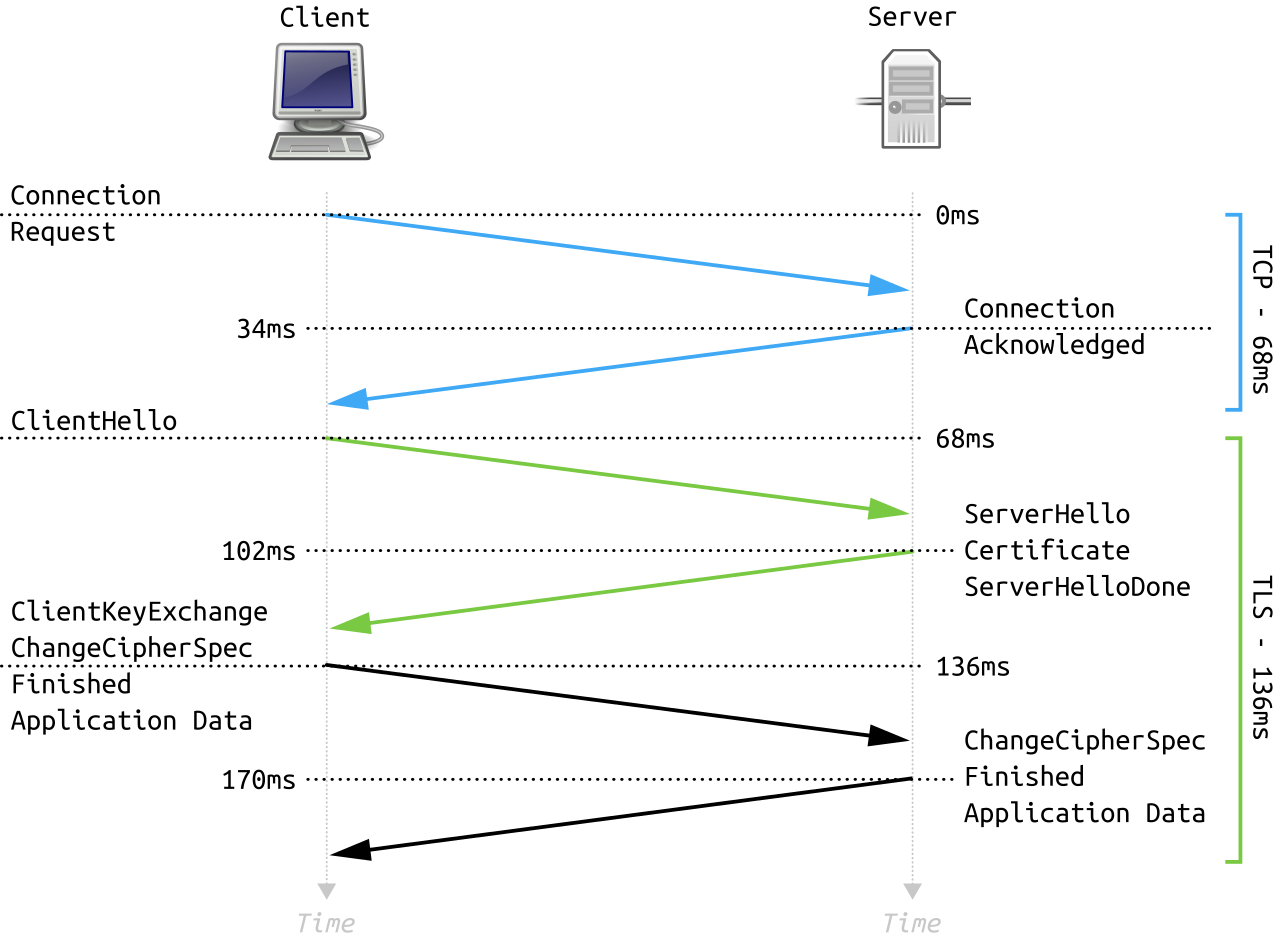
(Fleshgrinder, Public domain, via Wikimedia Commons)
When you establish an HTTPS connection, the TCP layer is established first and then the TLS handshake happens. The handshake can be seen above is sort of like the TCP handshake: information is sent back and forth to set up the channel and make sure all the cryptographic side of things match up.
Primarily a certificate is exchanged, confirmed as valid, and then a (symmetric) encryption cipher is selected, as well as the pre-shared private key, and then the certificate is (sort of) put the side and the symmetric algorithm takes over.
The TLS certificate is something you're going to be working with a lot and need to understand fairly well.