Access Control List#
A good example of the ACL security model is the Linux file permissions model. We'll cover this concept in more detail later on in the course, but let's look at a simple example: rwxr-xr-x michaelc staff
We have three elements here:
- The ACL list:
rwxr-xr-x - The owner of the object:
michaelc - The group that owns the object:
staff
The ACL list defines who can access this resource, and how. In this example, we can break the ACL list up into three groups:
- Owner permissions:
rwx - Group permissions:
r-x - Other permissions:
r-x
This means the owner - michaelc - can read (r), write (w), and execute (x) this object. The group, called staff, can read and execute this object. Everyone else on the system ("Other") have the same permissions as the group.
The resource as an ACL attached to it. When it's accessed by a user or some process/thread (processes/threads run as a particular user and take that user's permissions), the ACL is consulted to determine if that user can access that resource.
Look at the screenshot below and you'll see the ACL for a random file on my macOS system:
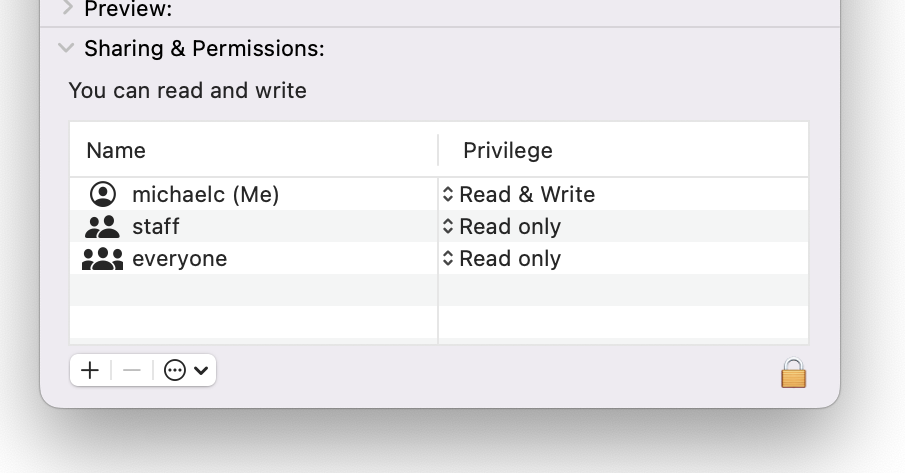
The concept is the same as Linux: we have a list with the Name of the user or group, and the Privilege they have on this file (object).
So ACLs are lists of permissions.