Single-factor Authentication#
This is the weakest, worst form of authentication. This is generally what most systems operate on and the common form is the classic username and password.
This form of authentication is considered bad because once the password has been leaked, cracked, observed, captured, or however else someone might get the password, the system account is compromised. What's worse is most people use the same password for almost all their accounts, so if the password is compromised all the accounts using it are also compromised.
A great system called "have i been pwned?" is the best source of information regarding bad passwords and password reuse. Check this out:
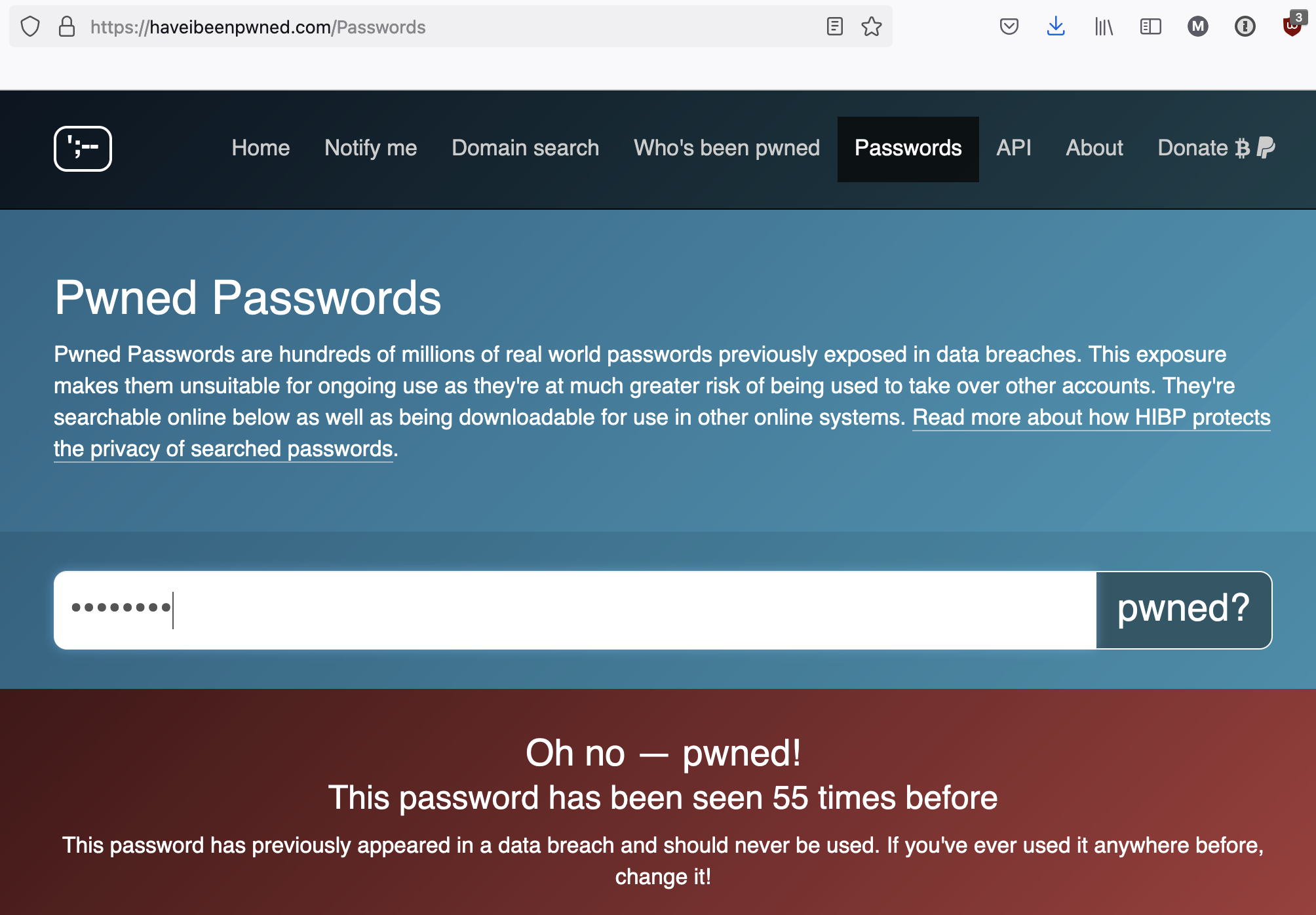
I used the password Monday67. That might be a silly password to you, but check out the top 10 (out of 20) worst passwords:
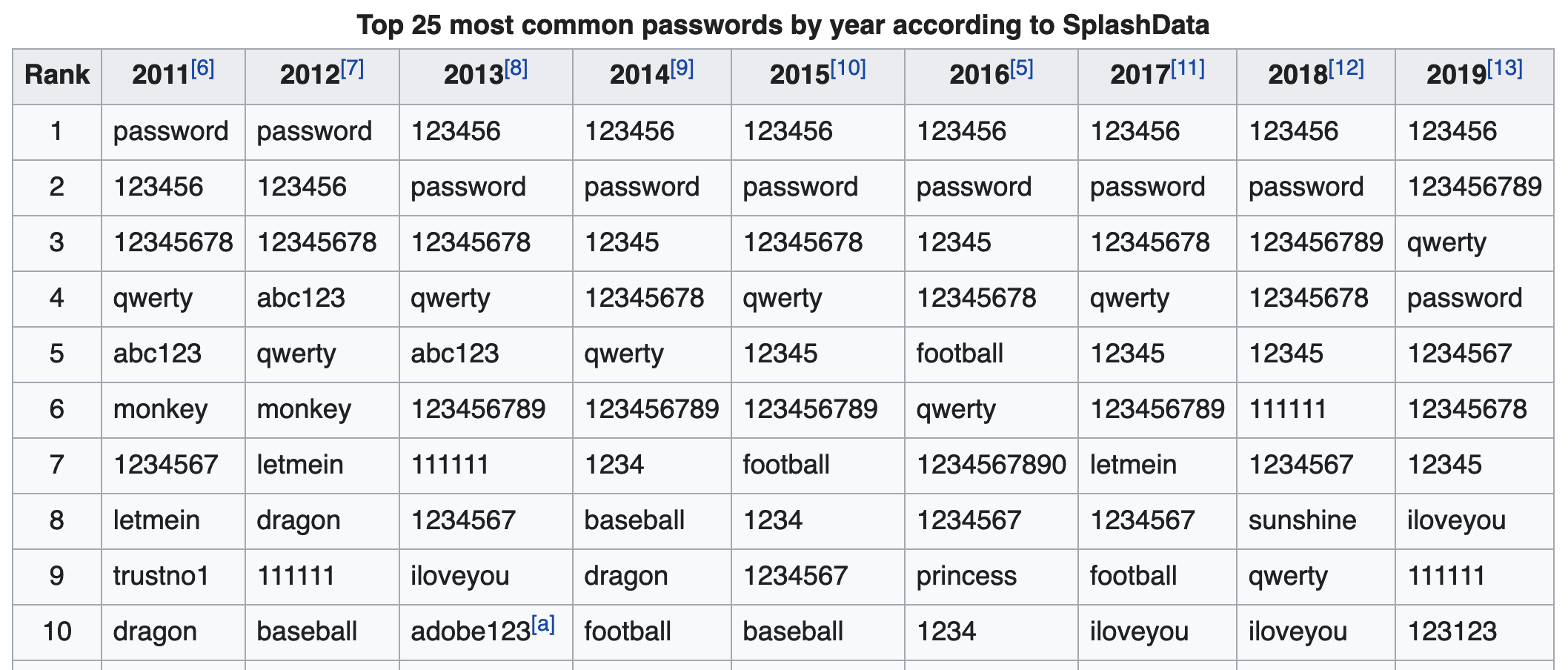
(https://en.wikipedia.org/wiki/List_of_the_most_common_passwords#SplashData)
Is it actually that far fetched that someone's password might be Monday67? Now consider that those passwords are seen so much because they're repeated, over and over, by the same people across multiple accounts.
A password is something the user knows.
The solution to this is, to start with, is simple: use a complex password (or passphrase) and make sure it's completely unique for each system you have access to.
But this is being heavily phased out for the next best thing...