Evaluation Workflow#
This is an advanced topic. We'll cover one key rule (Deny/Allow/Deny), and then briefly explore the primarily evaluation logic used by AWS for (most) policies. The latter is quite advanced and involves a lot of advanced topics we don't explore until Level Two and Level Three of this career path.
So we've setup a user and a role, and made some simple policies. What we don't know at this point is how AWS evaluates these policies to determine if you have permission to do something.
Well there is a single, overarching rule that we can follow that helps us to understand how things work: Deny, Allow, Deny. Let's break this down further.
- IAM's default response to any request in
Deny- don't allow anything! - If there is something that
Allows the request, then theDenyis overridden and the request is permitted - But! If just one policy exists that
Denys the request you're trying to make, known as an "explicit deny", then the request is blocked
So all requests are denied except when you explicitly say they're allowed, but if something explicity says it's denied, then the request is denied. I think we should visualise this:
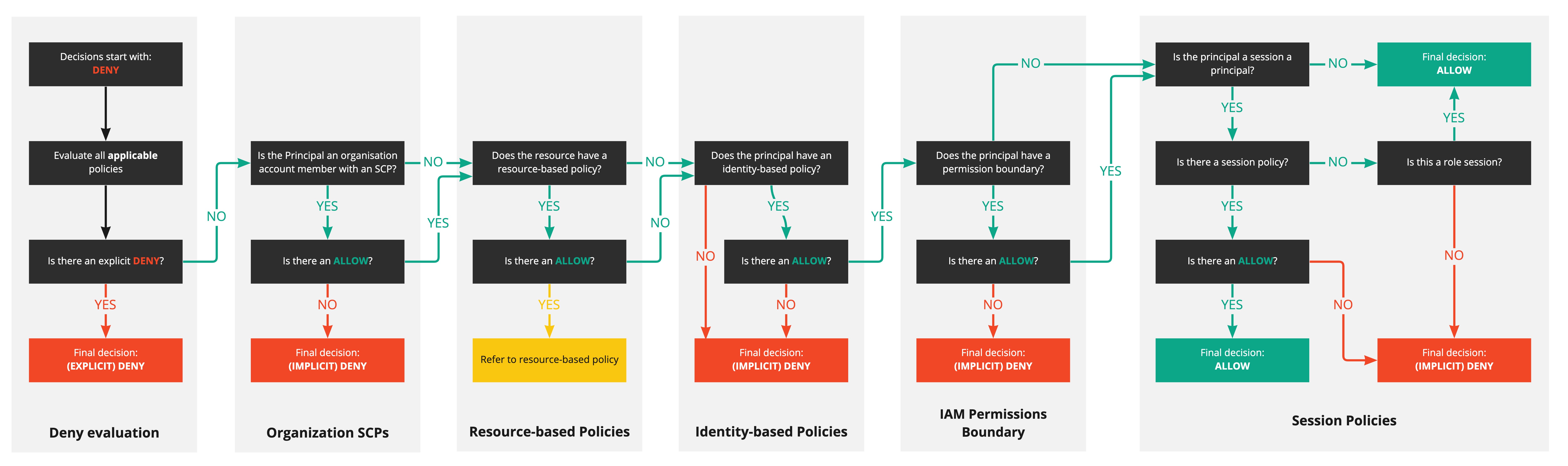
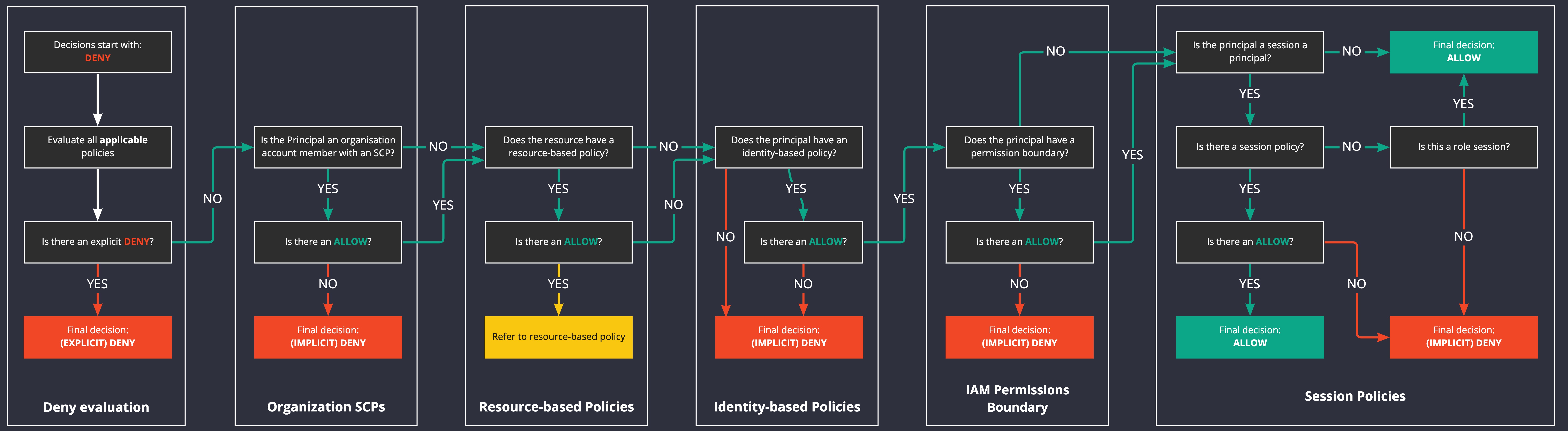
This looks really complicated, and it can be, but we're learning the basics of IAM here, and that's why I want you to remember: Deny, Allow, Deny.
When we start writing policies, we can go over this concept again (and again) and it'll become more obvious. To put that another way, despite the fact this is clearly "mechanical" and a flow chart, it times experience, doing it, and builds experience and a deep(er) understanding of this evaluation work flow.
So for now, let's leave this there and get to the doing part.