Elastic Cloud Compute (EC2)#
Now we've come to a topic that's definitely more exciting than the previous ones. EC2 is a service that lets us create Virtual Machines (VMs) called "Instances". These VMs will have an Operating System (OS) installed on them (we get to decide which one) which we can use to run software and provide networked servies, such as web sites, APIs, video streaming, gaming servers, and more.
This is a big topic, so we'll cover what you need to know to get the basics covered and later sections will cover more advanced detals and topics.
IAM Permissions#
To enable us to managed EC2 resources (and some networking resources), we will use the AmazonEC2FullAccess managed role. Attach this role to the cloud-admin user and login.
At this point, our cloud-admin user now has AmazonEC2FullAccess and NetworkAdministrator. Those permissions are already growing, and we're going to be adding in more as we move through this section. Now you should be able to see why IAM credentials are high-risk.
Info
In fact, check out this screenshot from the 2022 Uber cyber security breach in which a hacker got access to their AWS account:
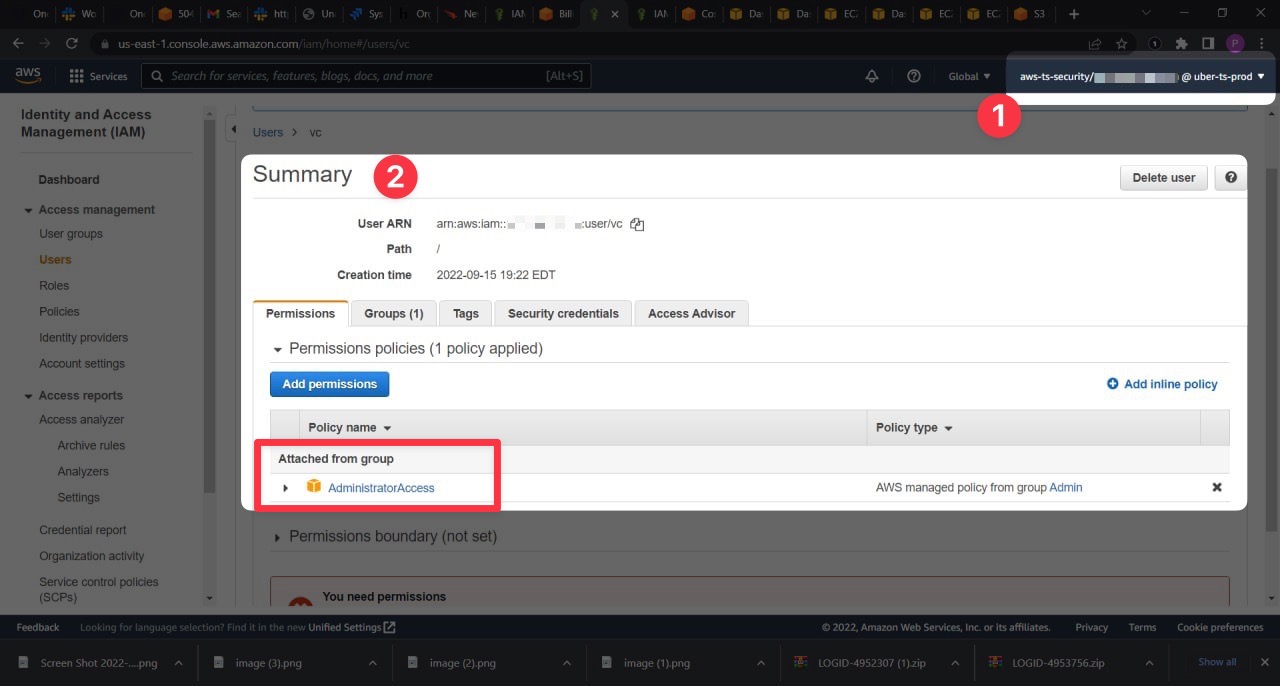
- That's the account they've hacked into
- And this is an account they now have access to -
AdministratorAccess
The AdministratorAccess role can do virtually anything in an AWS account. Anything. This is why we keep our user's IAM permissions tightly bound, and this is why we take IAM security very seriously.
We'll make sure to delete our credentials further down the line.